This blog is made for Expressing My Ideas, Views, and to put some technical datas.
Tuesday, April 27, 2010
Wget
Its features include recursive download, conversion of links for offline viewing of local HTML, support for proxies, and much more. It appeared in 1996, coinciding with the boom of popularity of the Web, causing its wide use among Unix users and distribution with most major Linux distributions. Written in portable C, Wget can be easily installed on any Unix-like system and has been ported to many environments, including Mac OS X, Microsoft Windows, OpenVMS and AmigaOS.
It has been used as the basis for graphical programs such as GWget for the GNOME Desktop and KGet for the KDE Desktop. Wget is free software.
Using Wget
Basic usage
Typical usage of GNU Wget consists of invoking it from the command line, providing one or more URLs as arguments.
# Download Wget's source code from the GNU ftp site.
wget ftp://ftp.gnu.org/pub/gnu/wget/wget-latest.tar.gz
wget http://www.example.com/
Advanced usage
# Using wget to download content protected by referer and cookies.
# 1. get base url and save its cookies in file
# 2. get protected content using stored cookies
wget --cookies=on --keep-session-cookies --save-cookies=cookie.txt http://first_page
wget --referer=http://first_page --cookies=on --load-cookies=cookie.txt
--keep-session-cookies --save-cookies=cookie.txt http://second_page
For more information see the man page of wget.
Authors and copyright
GNU Wget was written by Hrvoje Nikšić with contributions by many other people, including Dan Harkless, Ian Abbott, and Mauro Tortonesi. Significant contributions are credited in the AUTHORS file included in the distribution, and all remaining ones are documented in the changelogs, also included with the program. Wget is now maintained by Micah Cowan.
The copyright to Wget belongs to the Free Software Foundation, whose policy is to require copyright assignments for all non-trivial contributions to GNU software.
Thanks to : wikipedia
cal (Unix)
$ cal
April 2010Thanks to : Wikipedia
Su Mo Tu We Th Fr Sa
1 2 3
4 5 6 7 8 9 10
11 12 13 14 15 16 17
18 19 20 21 22 23 24
25 26 27 28 29 30
lp (Unix)
* lp is the standard name for the UNIX System V printer command.
* The Common Unix Printing System, used on Linux and Mac OS X among other systems, uses lp as the primary program for job assignment.
* The LPRng project provides lp as a simple wrapper to the lpr command.
* Plan 9 from Bell Labs uses a command called lp for printing, though its functionality is somewhat different and simplified from the System V version. It is actually written as an rc shell script.
Thanks to
http://en.wikipedia.org/wiki/Lp_(Unix)
strace
A similar utility is provided by Cygwin.
Usage
The most common usage is to start a program using strace, which prints a list of system calls made by the program. This is useful if the program continually crashes, or does not behave as expected; for example using strace may reveal that the program is attempting to access a file which does not exist or cannot be read.
An alternative application is to use the -p flag to attach to a running process. This is useful if a process has stopped responding, and might reveal, for example, that the process is blocking whilst attempting to make a network connection.
As strace only details system calls it cannot be used to detect as many problems as a code debugger such as GNU Debugger (gdb). It is, however, easier to use than a code debugger, and is an extremely useful tool for system administrators.
Example strace output
The following is an example of typical output of the strace command :
$ strace ls
output as follows :
execve("/bin/ls", ["ls"], [/* 42 vars */]) = 0
brk(0) = 0x8a6f000
access("/etc/ld.so.nohwcap", F_OK) = -1 ENOENT (No such file or directory)
mmap2(NULL, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0xb7f83000
access("/etc/ld.so.preload", R_OK) = -1 ENOENT (No such file or directory)
open("/etc/ld.so.cache", O_RDONLY) = 3
fstat64(3, {st_mode=S_IFREG|0644, st_size=60808, ...}) = 0
mmap2(NULL, 60808, PROT_READ, MAP_PRIVATE, 3, 0) = 0xb7f74000
close(3) = 0
access("/etc/ld.so.nohwcap", F_OK) = -1 ENOENT (No such file or directory)
open("/lib/tls/i686/cmov/librt.so.1", O_RDONLY) = 3
read(3, "\177ELF\1\1\1\0\0\0\0\0\0\0\0\0\3\0\3\0\1\0\0\0\240\30\0\0004\0\0\0\240"..., 512) = 512
fstat64(3, {st_mode=S_IFREG|0644, st_size=30624, ...}) = 0
mmap2(NULL, 33364, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0xb7f6b000
mmap2(0xb7f72000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x6) = 0xb7f72000
close(3) = 0
access("/etc/ld.so.nohwcap", F_OK) = -1 ENOENT (No such file or directory)
open("/lib/libselinux.so.1", O_RDONLY) = 3
read(3, "\177ELF\1\1\1\0\0\0\0\0\0\0\...............................
.....................
.....................
The above fragment is only a small part of the output of strace when run on the 'ls' command. It shows that the current working directory is opened, inspected and its contents retrieved. The resulting list of file names is written to standard output.
Thanks to:
http://en.wikipedia.org/wiki/Strace
Monday, April 26, 2010
patch (Unix)
Usage context
Developed by a programmer for other programmers, patch was frequently used for updating of source code to a newer version. Because of this many people came to associate patches with source code, whereas patches can in fact be applied to any text. It should be noted that patched files do not accumulate any unneeded text, which is what some people perceive based on the English meaning of the word; patch is as capable of removing text as it is of adding it.
Patches described here should not be confused with binary patches, which, although can be conceptually similar, are distributed to update binary files comprising the program to a new release.
Patches in software development
The diff files that serve as input to patch are readable text files, which means that they can be easily reviewed or modified by humans before use.
In addition to the "diff" program, diffs can also be produced by other programs, such as Subversion, CVS, RCS, Mercurial and Git.
Patches have been the crucial component of many source control systems, including CVS.
Usage examples
To create a patch, one could run the following command in a shell:
$ diff -u oldFile newFile > mods.diff # -u tells diff to output unified diff format
To apply a patch, one could run the following command in a shell:
$ patch < mods.diff
This tells patch to apply the changes to the specified files described in mods.diff. Patches to files in subdirectories require the additional -pnumber option, where number is 1 if the base directory of the source tree is included in the diff, and 0 otherwise.
Patches can be undone, or reversed, with the '-R' option:
$ patch -R < mods.diff
If the file is not identical to the version the diff was generated against, the patch will not be able to be applied cleanly. For example, if lines of text are inserted at the beginning, the line numbers referred to in the patch will be incorrect. patch is able to recover from this, by looking at nearby lines to relocate the text to be patched. It will also recover when lines of context (for context and unified diffs) are altered; this is described as fuzz.
Ports of patch
Originally written for Unix and Unix-like systems, patch has also been ported to Windows and many other platforms. Windows ports of patch are provided by GnuWin32 and UnxUtils.
Thanks to :
http://en.wikipedia.org/wiki/Patch_(Unix)
Saturday, April 24, 2010
grep
grep- Fine-Tune Your Searches
| To Find… | Use This Option | Example |
|---|---|---|
| Text in subfolders | -r | grep -r Walden ~/Documents/*Finds Walden in any file in any subfolder of ~/Documents. |
| Whole words only | -w | grep -w liveFinds only live ; does not find liver , lives , lived , and so on. |
| Case-insensitive text | -i | grep -i pondFinds pond , POND , or Pond . |
| File names only | -l | grep -l WaldenFinds files containing Walden , but returns only a list of file names. |
| Number of occurrences only | -c | grep -c WaldenReturns the names of files containing Walden and the number of hits in each file. |
grep: Searching for Words
grep
Within Linux (or any other UNIX), many people make use of filters, small programs (black boxes) that read input from standard input (stdin), do something with this input, and return the result to standard output (stdout).
Linux has many filters. Some examples are:
wc: print the number of bytes, words and lines in a file
tr: translate or delete characters
grep: print lines matching a pattern
sort: sort lines in a file
cut: cut selected fields from a file
The easiest way to learn these filters is to use them. This may seem daunting at first, since you may not know all the capabilities of these filters. I will describe the functions of grep so that you can benefit from its power.
I will be using this article (article.txt) as the input file for all the examples.
The syntax of the grep command is as follows:
grep [ -[[AB] ]num ] [ -[CEFGVBchilnsvwx] ][ -e ] pattern| -file ] [ files... ]
I use GNU grep Version 2; if you're using another version, you may have slightly different options. I will touch on only those options I use most. To learn more about the grep command, see the man page. Variants of the grep command are egrep and fgrep. grep includes flags to simulate these commands: -E for egrep and -F for fgrep.
The simplest form of the command is:
grep flip article.txt
This will search for the word “flip” in the file article.txt and will display all lines containing the word “flip”.
grep also accepts regular expressions, so to search for “flip” in all files in the directory, the following command can be given:
grep flip *
All lines in all files which contain the word “flip” will be displayed, preceded by the file name. Thus, the first line of the output will look like this:
article.txt:grep flip article.txtThe line begins with the name of the file containing the word “flip”, followed by a colon, then the appropriate line.
Sometimes you may want to define the search for special characters or a word combination. To do this, put the expression between quotes so that the whole expression/pattern will be treated as one. The command would then look like this:
grep -e "is the"
I put the -e (i.e., do pattern search) option in this example just for demonstration purposes. It is not necessary to specify, as it is the default value.
To see the line numbers in which the pattern is found, use the -n option. The output will look like that shown above, with the file name replaced by the line number before the colon.
Another option which provides us with a number is the -c option. This option outputs the number of times a word exists in a file. This article contains the word “flip” 10 times.
> grep -c flip article.txt
10
You may now be able to think of many ways in which you might use grep. For any command you use often, speed is important. Normally, grep can do its job quickly. However, if the search is being done over many large files, the results will be slower to return. In this case, you can speed up the process by using either fgrep or egrep. fgrep is used only for finding strings, and egrep is used for complicated regular expressions.
File names, words, sentences and numbers can all be found quickly using grep. In addition, using the grep command together with other filters can be very powerful and prove to be of great value. For example, you could search a statistics file and sort the output by piping it through the sort and cut commands (see man pages):
grep ... | sort ... | grep ... | cut ... > result
This has been a quick introduction to get you started and rouse your curiosity to learn more about grep and other filters.
Thanks to :
http://www.linuxjournal.com/article/2384
Tuesday, April 20, 2010
Asynchronous serial communication
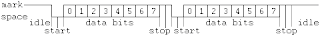 In the diagram, a start bit is sent, followed by seven data bits, a parity bit and one "stop bit", for a 10-bit character frame. The number of data and formatting bits, the order of data bits, and the transmission speed must be pre-agreed by the communicating parties.
In the diagram, a start bit is sent, followed by seven data bits, a parity bit and one "stop bit", for a 10-bit character frame. The number of data and formatting bits, the order of data bits, and the transmission speed must be pre-agreed by the communicating parties.The "stop bit" is actually a "stop period"; the stop period of the transmitter may be arbitrarily long. It cannot be shorter than a specified amount, usually 1 to 2 bit times. The receiver requires a shorter stop period than the transmitter. At the end of each character, the receiver stops briefly to wait for the next start bit. It is this difference which keeps the transmitter and receiver synchronized.
Thanks to:
http://en.wikipedia.org/wiki/Asynchronous_serial_communication
Thursday, April 15, 2010
Twitux : enter password for default keyring to unlock - solution
Today I was fiddling around my Ubuntu ( jaunty ) desktop . I installed twitux , a twitter client and was happy with it. I switched off the machine and went for lunch. When I came back, twitux started asking this.
"enter password for default keyring to unlock
The application 'Twittux
wants access to the default keyring but it is locked"
I tried out my default login password. But could not start twitux.
I searched on net and finally arrived at a solution.
Here it is.
$ cd ~/.gnome2/keyrings
$ rm deault.keyring
That fixed my problem. The next time I started twitux, it asked me to setup a new password for the key ring.
Wednesday, April 14, 2010
C Programming FAQs Part1
/*************************************************************************/
#define int char
main()
{
int i=65;
printf("sizeof(i)=%d \n",sizeof(i));
}
/*Answer:
sizeof(i)=1
Explanation:
Since the #define replaces the string int by the macro char
*/
/*************************************************************************/
void main()
{
int const * p=5;
printf("%d",++(*p));
}
/*************************************************************************/
main()
{
char s[ ]="man";
int i;
for(i=0;s[ i ];i++)
printf("%c%c%c%c \n",s[ i ],*(s+i),*(i+s),i[s]);
}
/*
Explanation:
s[i], *(i+s), *(s+i), i[s] are all different ways of expressing the
same
idea. Generally array name is the base address for that array. Here s
is
the base address. i is the index number/displacement from the base
address. So, indirecting it with * is same as s[i]. i[s] may be
surprising. But in the case of C it is same as s[i].*/
/*************************************************************************/
main()
{
static int var = 5;
printf("%d ",var--);
if(var)
main();
}
/*
Explanation:
When static storage class is given, it is initialized once. The change
in
the value of a static variable is retained even between the function
calls. Main is also treated like any other ordinary function, which can
be
called recursively.*/
main()
{
int c[ ]={2.8,3.4,4,6.7,5};
int j,*p=c,*q=c;
for(j=0;j<5;j++) {
printf(" %d ",*c);
++q; }
for(j=0;j<5;j++){
printf(" %d ",*p);
++p; }
}
/*
Answer:
2 2 2 2 2 2 3 4 6 5
Explanation:
Initially pointer c is assigned to both p and q. In the first loop,
since
only q is incremented and not c , the value 2 will be printed 5 times.
In
second loop p itself is incremented. So the values 2 3 4 6 5 will be
printed.
*/
/*************************************************************************/
main()
{
extern int i;
i=20;
printf("%d",i);
}
/*
Answer:
Linker Error : Undefined symbol '_i'
Explanation:
extern storage class in the following declaration,
extern int i;
specifies to the compiler that the memory for i is allocated in some
other
program and that address will be given to the current program at the
time
of linking. But linker finds that no other variable of name i is
available
in any other program with memory space allocated for it. Hence a linker
error has occurred .
*/
/*************************************************************************/
main()
{
int i=-1,j=-1,k=0,l=2,m;
m=i++&&j++&&k++||l++;
printf("%d %d %d %d %d",i,j,k,l,m);
}
/*Explanation :
Logical operations always give a result of 1 or 0 . And also the
logical
AND (&&) operator has higher priority over the logical OR (||)
operator.
So the expression �i++ && j++ && k++� is executed first. The result of
this expression is 0 (-1 && -1 && 0 = 0). Now the expression is 0 ||
2
which evaluates to 1 (because OR operator always gives 1 except for �0
||
0� combination- for which it gives 0). So the value of m is 1. The
values
of other variables are also incremented by 1.
*/
/*************************************************************************/
main()
{
char *p;
printf("%d %d \n",sizeof(*p),sizeof(p));
}
/*
Answer:
1 2
Explanation:
The sizeof() operator gives the number of bytes taken by its operand. P
is
a character pointer, which needs one byte for storing its value (a
character). Hence sizeof(*p) gives a value of 1. Since it needs two
bytes
to store the address of the character pointer sizeof(p) gives 2.
*/
/*************************************************************************/
main()
{
int i=10;
i=!i>14;
printf("i=%d \n",i);
}
/*
Answer:
i=0
Explanation:
In the expression !i>14 , NOT (!) operator has more precedence than>
symbol. ! is a unary logical operator. !i (!10) is 0 (not of true is
false). 0>14 is false (zero).
*/
/* http://www.c.happycodings.com/Beginners_Lab_Assignments/code24.html */
/*************************************************************************/
Thanks to :
How to configure Gmail in your Evolution inbox
You can check if you have it or not by going to your Gmail account, them Settings. Check that on the top menu says “Forwarding and POP/IMAP” instead of just “Forwarding and POP”.
If not, make sure your language is set to “English (US)”.
If/when you do have the option, go to the menu and check the “Enable IMAP” radio button.
Now open your Evolution client and add the following settings:
=> Identity Tab
- Full Name: Name you’d like to be displayed on your messages
- Email Address: You full Gmail address
=> Receiving E-mail
Server Type: IMAP
Server: imap.gmail.com:993
Username: Your complete Gmail address
Security: SSL
Authentication Type: Password
Remember Password: Check (optional)
=> Sending E-mail
Server Type: SMTP
Server: smtp.gmail.com:587
Server Requires Authentication: Check
Security: TLS
Authentication Type: Login
Username: Your complete Gmail address
Remember Password: Check (optional)
After that click on send and receive. You should start getting your messages. I’ve heard some people saying that they had to restart Evolution for it to start working (also complaints that IMAP on Evolution is really slow).
You will see the folders added to the left pane of your Evolution inbox.
Monday, April 12, 2010
How to connect two systems using a ethernet cable and make one as gateway and browse internet
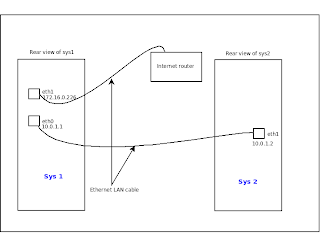
for sys1 :
For configuring the sys1 as the ip address of 10.0.1.1
$ sudo ifconfig eth0 10.0.1.1 netmask 255.255.255.0 broadcast 10.0.1.255
for sys2 :
For configuring the sys2 as the ip address of 10.0.1.2
$ sudo ifconfig eth0 10.0.1.2 netmask 255.255.255.0 broadcast 10.0.1.255
for sys1
siva@ubuntu:~$ /sbin/ifconfig
eth0 Link encap:Ethernet HWaddr 00:24:1d:28:93:97
inet addr:10.0.1.1 Bcast:10.0.1.255 Mask:255.255.255.0
inet6 addr: fe80::224:1dff:fe28:9397/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:73 errors:0 dropped:0 overruns:0 frame:0
TX packets:54 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:13801 (13.8 KB) TX bytes:9044 (9.0 KB)
Interrupt:253 Base address:0xa000
eth1 Link encap:Ethernet HWaddr 00:e0:5c:00:27:1f
inet addr:172.16.0.226 Bcast:172.16.255.255 Mask:255.255.0.0
inet6 addr: fe80::2e0:5cff:fe00:271f/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:4968 errors:0 dropped:0 overruns:0 frame:0
TX packets:5438 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:3325051 (3.3 MB) TX bytes:1119263 (1.1 MB)
Interrupt:21 Base address:0xce00
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:4 errors:0 dropped:0 overruns:0 frame:0
TX packets:4 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:240 (240.0 B) TX bytes:240 (240.0 B)
for sys1
$ siva@ubuntu:~$ sudo echo 1 > /proc/sys/net/ipv4/ip_forward
else
$ siva@ubuntu:~$ chmod +x /tmp/forward.sh
$ sudo echo 1 > /proc/sys/net/ipv4/ip_forward
$ sudo /tmp/forward.sh
siva@ubuntu:~$ route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
10.0.1.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
169.254.0.0 0.0.0.0 255.255.0.0 U 1000 0 0 eth1
172.16.0.0 0.0.0.0 255.255.0.0 U 1 0 0 eth1
0.0.0.0 172.16.0.6 0.0.0.0 UG 0 0 0 eth1
Now configure ip address of 10.0.1.1 sys1 as gateway in sys2
for sys2 :
$ root@localhost.com # /sbin/rout add default gw 10.0.1.1
for sys2 :
$ ping 10.0.1.1
You have to configure your destination IP and gateway IP in the internet router. then follow the steps as
for sys2 :
$ ping 172.16.0.2
for sys2 :
$ ping www.google.com
In sys2 :
$ root@localhost.com # :~$ ping www.google.com
PING www.l.google.com (209.85.231.104) 56(84) bytes of data.
64 bytes from maa03s01-in-f104.1e100.net (209.85.231.104): icmp_seq=1 ttl=56 time=28.4 ms
64 bytes from maa03s01-in-f104.1e100.net (209.85.231.104): icmp_seq=2 ttl=56 time=28.5 ms
64 bytes from maa03s01-in-f104.1e100.net (209.85.231.104): icmp_seq=3 ttl=56 time=27.8 ms
C-c C-c
--- www.google.com ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 27.802/28.261/28.577/0.332 ms
I think so this tutorial will be easier to configure.
How to communicate between two ubuntu systems using a Ethernet cable
To setup ip addresses from console is not very hard. Here is what I would do:
You can set ip address with ifconfig command. That kind of setting will not be remembered after you reboot, but will be enough to set up local network between two computers for transfering files (that is what I do when I need to transfer files from my laptop to my home computer). On your laptop you should type (in console):
ifconfig eth0 10.0.1.1 netmask 255.255.255.0 broadcast 10.0.1.255
And on your home computer:
ifconfig eth0 10.0.1.2 netmask 255.255.255.0 broadcast 10.0.1.255
Two computers are now on the same network and can talk to each other. At this point I usually start ssh daemon on one of the computers. On suse you can start it from yast, and on ubuntu you may type (as root):
/etc/init.d/ssh start (or sudo /etc/init.d/ssh start)
Now you can connect to that machine via ssh, by typing:
ssh 10.0.1.1 (or 10.0.1.2)
or copy files with scp command, for example:
scp username@10.0.1.1:/home/username/Desktop/*.mp3 .
will copy all mp3 files from your Desktop folder on 10.0.1.1 machine to 10.0.1.2
Friday, April 9, 2010
Duty Cycle
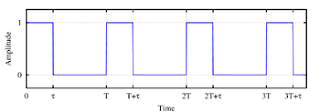
The duty cycle is the fraction of time that a system is in an "active" state. In particular, it is used in the following contexts:
Duty cycle is the proportion of time during which a component, device, or system is operated.Suppose a disk drive operates for 1 second, and is shut off for 99 seconds, then is run for 1 second again, and so on. The drive runs for one out of 100 seconds, or 1/100 of the time, and its duty cycle is therefore 1/100, or 1 percent.
In a periodic phenomenon, the ratio of the duration of the phenomenon in a given period to the period.
Duty cycle D = (τ/T)
where
τ is the duration that the function is active high (normally when the signal is greater than zero);
Τ is the period of the function.
For example, in an ideal pulse train (one having rectangular pulses), the duty cycle is the pulse duration divided by the pulse period. For a pulse train in which the pulse duration is 1 μs and the pulse period is 4 μs, the duty cycle is 0.25. The duty cycle of a square wave is 0.5, or 50%.
Thanks to :